








Tactical
Homeland
Unified
Network for
Disaster
Emergency
Response,
Strategic
Targeted
Reconnaissance and
Intelligence
Key
Efforts
The big idea
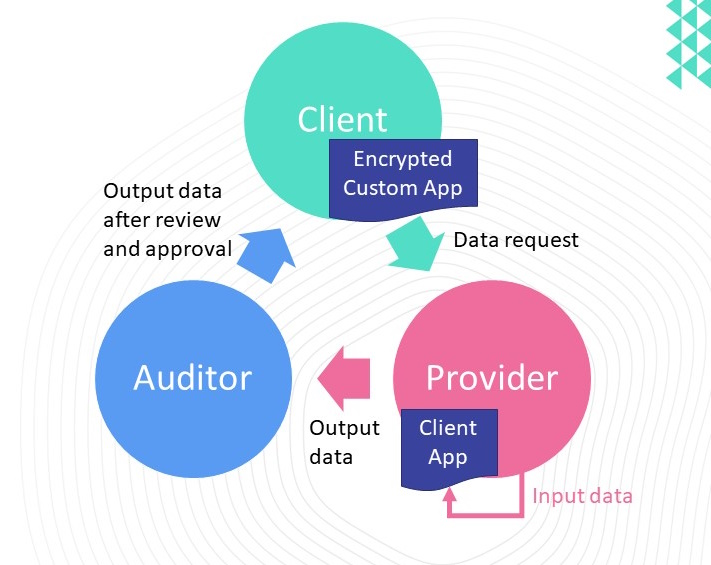
The need for a unified network to address the challenges of managing and analysing large amounts of
data across different domains is more pressing than ever. The unified network can provide a solution by
enabling the integration of data from different sources, allowing for more efficient data processing and
analysis.
In addition, a unified network can facilitate collaboration and information sharing between different
stakeholders, allowing for a more comprehensive and integrated approach to problem solving. A unified
network can also help to address issues of data fragmentation and inefficiencies in data processing.
It can also play a crucial role in helping to plan resource allocation, achieve better results in
resource-constrained situations and create a fully distributed data model.
Through the use of a fully distributed data model, the network can ensure that information is shared in
real time between all agencies and organisations involved, enabling rapid and efficient decision making.
This approach can be particularly valuable in resource-constrained situations where agencies and
organisations need to work together to achieve the best possible outcome.
During crisis we need to optimize for:
- Allocation of available resources
- Maximize effect in resource-constrained situations
- Fully distributed data model allows for efficient data processing and analysis
Petabytes of Images
Hours Spent in the Hackathon
Images Processed
Project Revisions
Isolated data warehouses
- Hard to gather and process
- Limited embedded knowledge
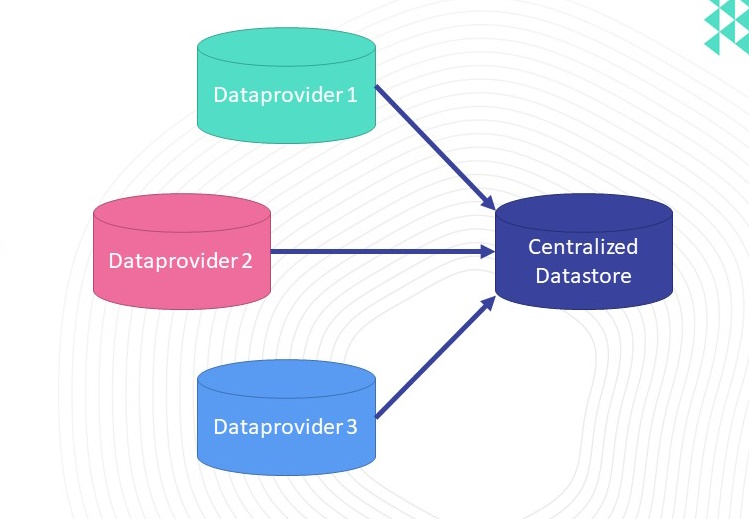
Attempts to centralize data
- Unethical surveillance practices
- Attack vector
- Inability to reuse / Inefficient
.gif)
.gif)
.gif)
.gif)
.gif)
.gif)




